Companies See Work From Home As A Security Threat
PYMNTS
SEPTEMBER 27, 2020
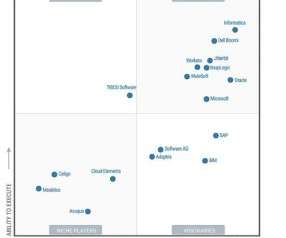
About 70 percent of the 500 companies surveyed said that they expected remote working during the pandemic to increase the cost of a breach; four-fifths told researchers said they expected it will take longer to notice and secure a breach.














































Let's personalize your content