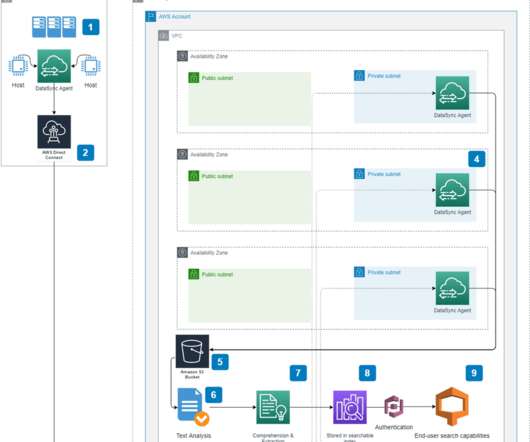
Expand your search using AWS native services to identify, comprehend and securely store documents.
Perficient
JANUARY 11, 2021
The document debacle. Companies continue to fight the battle of the age-old problem: paper documents. Adapting to document modernization to expand the ability to search, catalog and protect HIPAAPII data is paramount. It is based on the Apache Lucene engine and is suitable for large document indexing and search capabilities.














































Let's personalize your content