How to control sensitive data on unmanaged devices with MCAS
Perficient
MARCH 21, 2021
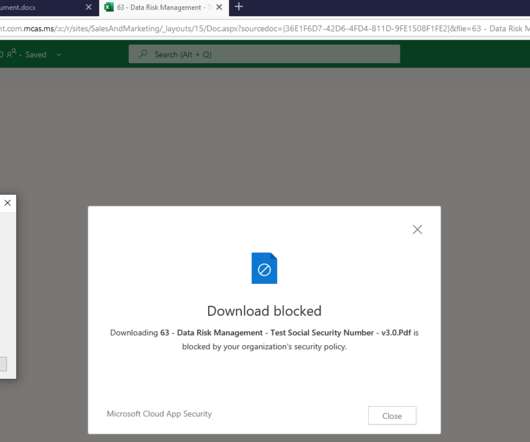
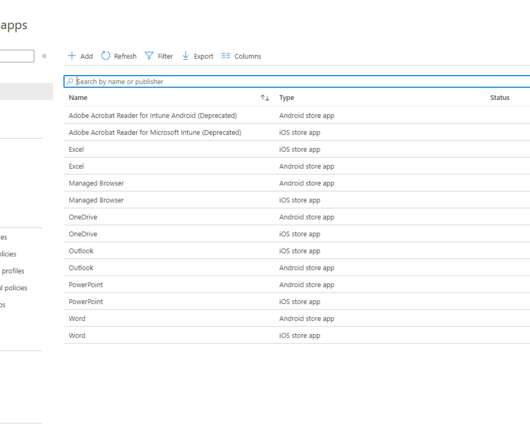
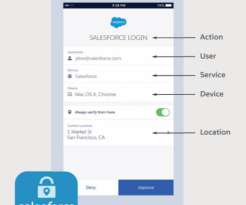
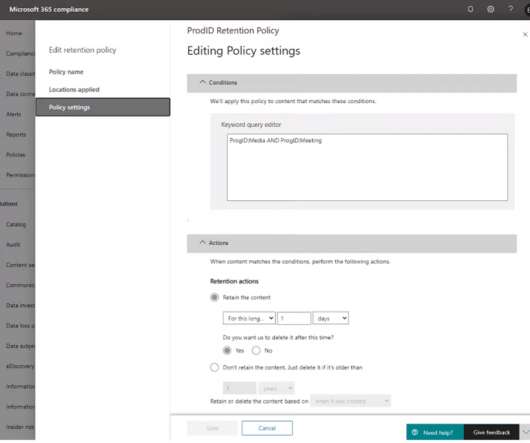
In today’s blog, I’ll show you how you can block downloading of files with sensitive data to unmanaged devices with the use of session policies in Microsoft Cloud App Security (MCAS). Megan is working on a file that has several different Social Security Numbers of different employees at her organization.








































Let's personalize your content