Securing Teams with built-in apps in Microsoft Endpoint Manager
Perficient
NOVEMBER 15, 2020
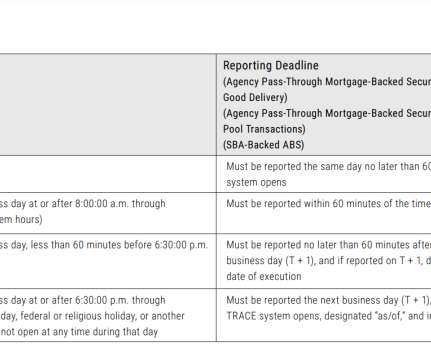
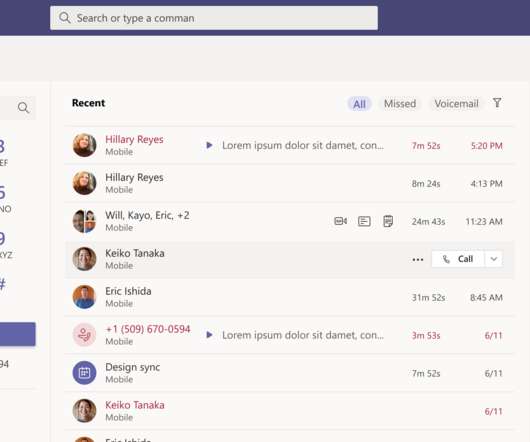
labor force working remotely, managing devices has become more important than ever. Luckily, Microsoft has made great advancements in device management capabilities, many of which we’ll discuss today. In this blog, we’ll go over four main areas of Endpoint Management: Creating an app deployment. Securing the App.











































Let's personalize your content