What Is Not Considered a TRACE-Eligible Security and What Should Not Be Reported
Perficient
JULY 18, 2022
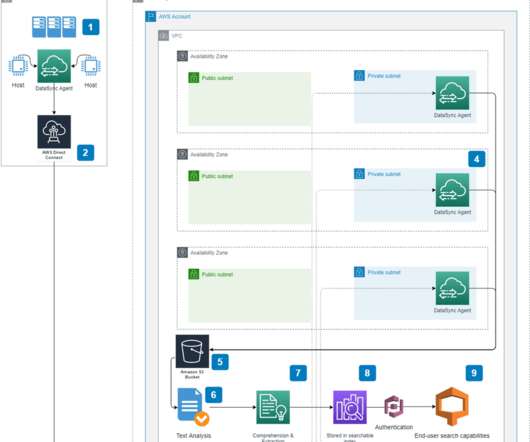
A TRACE-eligible security does not include a debt security that is issued by a foreign, sovereign government or a money market instrument. Transfers of securities made pursuant to an asset purchase agreement (APA) that is subject to a hearing in a bankruptcy court. What Information Must Be Included in a TRACE Trade Report?











































Let's personalize your content